Why Kenyans do it better
Thursday, December 8, 2016
Thursday, November 17, 2016
Fake USB Chargers that Wirelessly Record
Beware of Fake USB Chargers that Wirelessly Record Everything You Type, FBI warns

Dubbed KeySweeper, the device included a web-based tool for live keystroke monitoring and was capable of sending SMS alerts for typed keystrokes, usernames, or URLs, and work even after the nasty device is unplugged because of its built-in rechargeable battery. Besides the proof-of-concept attack platform, security researcher Samy Kamkar, who created KeySweeper, also released instructions on how to build your own USB wall charger.
Now, it seems like hackers and criminal minds find this idea smart.
The FBI has issued a warning advisory for private industry partners to look out for highly stealthy keyloggers that quietly sniff passwords and other input data from wireless keyboards.
According to the advisory, blackhat hackers have developed their custom version of KeySweeper device, which "if placed strategically in an office or other location where individuals might use wireless devices", could allow criminals to steal:
- Intellectual property
- Trade secrets
- Personally identifiable information
- Passwords
- Other sensitive information
"The primary method of defense is for corporations to restrict the use of wireless keyboards. Since the KeySweeper requires over-the-air transmission, a wired keyboard will be safe from this type of attack." FBI advised.Sniffers work against wireless devices that do not use secure encryption for the data transmitted between a keyboard and the computer.
Share Excerpt
Wednesday, November 16, 2016
Researchers identify antibody that neutralizes 98% of HIV strains
An antibody from an HIV-infected person has successfully
neutralized 98 percent of HIV isolates tested, including the lion’s
share of strains resistant to other antibodies of the same class, US
scientists have found.
The striking efficiency of
the powerful antibody, named N6, makes it an ideal candidate for
further research to treat or prevent HIV infection, scientists from the National Institutes of Health, the largest biomedical research agency in the world, have stated.
Scientists scrutinized the evolution of N6 over time to understand how exactly it managed to develop the ability to potently neutralize the majority of HIV strains.
Researchers say that identifying broadly neutralizing antibodies against HIV has been a real challenge because the virus rapidly changes its surface proteins to avoid recognition by the immune system.
In 2010, scientists at National Institute of Allergies and Infectious Diseases (NIAID’s) Vaccine Research Center (VRC) discovered an antibody called VRC01 that can stop up to 90 percent of HIV strains from infecting human cells.
“Like VRC01, N6 blocks infection by binding to a part of the HIV envelope called the CD4 binding site, preventing the virus from attaching itself to immune cells,” researchers said in a press release published on Tuesday.
Findings from the latest study showed that N6 developed a “unique
mode of binding that depends less on a variable area of the HIV
envelope known as the V5 region and focuses more on conserved regions,
which change relatively little among HIV strains. This allows N6 to
tolerate changes in the HIV envelope, including the attachment of sugars
in the V5 region, a major mechanism by which HIV develops resistance to
other VRC01-class antibodies.”
The new findings suggest that N6 could pose advantages over VRC01, researchers noted, adding that due to its potency, N6 may offer "stronger and more durable prevention and treatment benefits, and researchers may be able to administer it subcutaneously (into the fat under the skin) rather than intravenously."
According to UNAIDS, there were approximately 36.7 million people worldwide living with HIV/AIDS at the end of 2015. Of these, 1.8 million were children younger than 15 years old. The vast majority of people living with HIV are from low- and middle-income countries.
The WHO estimated that currently only some 54 percent of people with HIV know their status.
Scientists scrutinized the evolution of N6 over time to understand how exactly it managed to develop the ability to potently neutralize the majority of HIV strains.
Researchers say that identifying broadly neutralizing antibodies against HIV has been a real challenge because the virus rapidly changes its surface proteins to avoid recognition by the immune system.
In 2010, scientists at National Institute of Allergies and Infectious Diseases (NIAID’s) Vaccine Research Center (VRC) discovered an antibody called VRC01 that can stop up to 90 percent of HIV strains from infecting human cells.
“Like VRC01, N6 blocks infection by binding to a part of the HIV envelope called the CD4 binding site, preventing the virus from attaching itself to immune cells,” researchers said in a press release published on Tuesday.
The new findings suggest that N6 could pose advantages over VRC01, researchers noted, adding that due to its potency, N6 may offer "stronger and more durable prevention and treatment benefits, and researchers may be able to administer it subcutaneously (into the fat under the skin) rather than intravenously."
According to UNAIDS, there were approximately 36.7 million people worldwide living with HIV/AIDS at the end of 2015. Of these, 1.8 million were children younger than 15 years old. The vast majority of people living with HIV are from low- and middle-income countries.
The WHO estimated that currently only some 54 percent of people with HIV know their status.
Tuesday, October 25, 2016
RAM, ROM, and Flash Memory
RAM, ROM, and Flash Memory
-
RAM: Stands for random access memory; refers to memory that the microprocessor can read from and write to. When you create something in memory, it’s done in RAM.RAM is memory and vice versa.
-
ROM: Stands for read-only memory. The microprocessor can read from ROM, but it can’t write to it or modify it. ROM is permanent. Often, ROM chips contain special instructions for the computer — important stuff that never changes. The microprocessor can access information stored on a ROM chip whenever it needs to. The instructions are always there because they’re not erasable.
-
Flash memory: A special type of memory that works like both RAM and ROM. You can write information to flash memory, like you can with RAM, but that information isn’t erased when the power is off, like it is with ROM.Sadly, flash memory isn’t as fast as RAM, so don’t expect it to replace standard computer memory any time soon.
If Earth is spinning to the east, why isn’t it faster to fly west?
If Earth is spinning to the east, why isn’t it faster to fly west?

Written by vicky
While Earth itself is spinning about 1,180 km/h to the east, the
ground and everything on it are travelling even faster – at about 1,670
km/h (1,037 mph). Even the air above the ground is travelling at around
this speed in an easterly direction. So for an aeroplane to get anywhere
at all, it has to be moving relative to the ground.
Say it’s travelling at 160 km/h (100 mph) – because it’s already moving at 1,670 km/h with the planet, plus that little bit extra, it’s able to keep itself ahead and actually get somewhere. On the other hand, if it’s travelling towards the west, it’s actually moving 1,670 km/h MINUS 160 km/h.
“Yes, to go west, you go east – just slower than Earth is going east,” says Henry Reich in the video above. “Unless you’re within 10 or so miles of the poles, in which case a brisk westerward walk will take you legitimately west.”
But it’s not so simple (we’re kidding – it was never simple), because winds in the upper atmosphere mess everything up. in the video above, but let’s just say it’s to do with different parts of Earth rotating at different speeds, because it’s a big, blue marble, and that’s what big blue marbles do when you spin them.
Say it’s travelling at 160 km/h (100 mph) – because it’s already moving at 1,670 km/h with the planet, plus that little bit extra, it’s able to keep itself ahead and actually get somewhere. On the other hand, if it’s travelling towards the west, it’s actually moving 1,670 km/h MINUS 160 km/h.
“Yes, to go west, you go east – just slower than Earth is going east,” says Henry Reich in the video above. “Unless you’re within 10 or so miles of the poles, in which case a brisk westerward walk will take you legitimately west.”
But it’s not so simple (we’re kidding – it was never simple), because winds in the upper atmosphere mess everything up. in the video above, but let’s just say it’s to do with different parts of Earth rotating at different speeds, because it’s a big, blue marble, and that’s what big blue marbles do when you spin them.
Tuesday, September 13, 2016
How to turn off Windows 10's keylogger (yes, it still has one)
Microsoft can track your keystrokes, your speech, and more. Here are the settings to turn it all off.
Last fall, I discussed the keylogger
that Microsoft openly put into the Windows 10 Technical Preview. The
company admitted that “we may collect voice information” and “typed
characters.” At the time I defended Microsoft, pointing out that the
Preview was “intended for testing, not day-to-day use,” and that
Microsoft recommended against installing the Preview on a computer with
sensitive files. I said that “I seriously doubt that the worst spyware
features will remain in the finished product.”
I was wrong.
I was wrong.
Microsoft pretty much admits it has a keylogger in its Windows 10 speech, inking, typing, and privacy FAQ:
“When you interact with your Windows device by speaking, writing
(handwriting), or typing, Microsoft collects speech, inking, and typing
information—including information about your Calendar and People (also
known as contacts)…”
If that makes you feel creepy, welcome to the human race.
Speaking of online Microsoft documents, you may want to browse the company’s overall Privacy Statement. To Microsoft’s credit, it’s in plain English rather than legalese. On the other hand, it’s about 17,000 words (as someone who’s paid by the word, I’m frankly jealous), so it will take time to find out if there’s anything else that’s truly awful inside.
The good news is that you can turn off the keylogging. Click Settings (it’s on the Start menu’s left pane) to open the Settings program. You’ll find Privacy...ummm....hold on a sec...OH! There it is!—on the very last row.
If that makes you feel creepy, welcome to the human race.
Speaking of online Microsoft documents, you may want to browse the company’s overall Privacy Statement. To Microsoft’s credit, it’s in plain English rather than legalese. On the other hand, it’s about 17,000 words (as someone who’s paid by the word, I’m frankly jealous), so it will take time to find out if there’s anything else that’s truly awful inside.
The good news is that you can turn off the keylogging. Click Settings (it’s on the Start menu’s left pane) to open the Settings program. You’ll find Privacy...ummm....hold on a sec...OH! There it is!—on the very last row.
Wednesday, July 20, 2016
5 best battery saver apps for Android
5 best battery saver apps for Android

Battery saving is a land of snake oil and half solutions. It truly is difficult to find an application that actually saves you battery since most battery saver measures are manual, including turning the brightness on your screen down, turning of mobile data when you’re not using it, and other tried and true methods. In many cases, it’s just a task manager with a battery saver name that can actually use more battery life than it’ll ever actually save. However, there are a few apps that can help out so let’s check out the best battery saver apps for Android. Please note that a couple of these are for root users only since root access can really help with battery saving measures.
Amplify (root only)
[Price: Free with in-app purchases]Amplify is a root-only application that gives you all kinds of control over various things that can save you battery life. With it, you can put a stop to wake locks (apps that wake up your device constantly, like Facebook), with the ability to control apps, alarms, and other services that could be draining your battery. The app is based on Material Design and it’s very easy to use, even for the non-tech savvy. It’s free to download with a pro version that adds additional features.
Get it now on Google Play!
Battery Saver 2016
[Price: Free]Battery Saver 2016 seems to shed all of the snake oil nonsense and sticks to the tried and true methods of helping you save battery life. The app will monitor other apps and let you know which ones are draining your battery more than they should be. It also contains toggles for WiFi, mobile data, GPS, Airplane Mode, Bluetooth, and others so you can manage your device’s sensors and radios to help you not use what you don’t need to use. There is even a brightness slider so you can turn your screen brightness down. It’s true that 90% of this is accessible in your Android Settings menu, but this is a fun little way to see all of it on one screen and it’s entirely free to use.
Get it now on Google Play!
Greenify
[Price: Free]Greenify is an app that can be used by root users or by non-root users alike. It’s kind of like Amplify in that it gives you detailed information about the applications that are waking up your device, how often they’re waking up your device, and how much time they spend once they initiate. For non-root users, you can use this information to start controlling the apps that cause problems while root users can start the Greenify service to make sure these apps stop waking up your device. It’s completely free to use, although there is an optional donate version if you want to support development.
Get it now on Google Play!
GSam Battery Monitor
[Price: Free / $2.49]GSam Battery Monitor is a comprehensive battery monitoring app that shows you what’s draining your device’s battery life. Its key feature is called App Sucker, where it takes a look at all the apps that are draining your battery so you can identify which ones are causing the problem. You can then take steps to make that app stop being such a drain on your battery. It’ll show you details on wake locks, wake time, and even CPU and sensor usage so you can see what’s really using what.
Get it now on Google Play!
Servicely (root only)
[Price: Free with in-app purchases]Servicely is a root-only application that aims to keep apps and services from running at the system level. The premise is easy to understand. You go through the application and find the apps that likely cause tons of wake locks and battery drain (looking at you, Facebook). Servicely then shuts those services down and prevents them opening back up which should, in theory, save you battery life. It has a slick interface and the core features are all free to use. It also comes with customization settings to let you use Servicely how you want.
Get it now on Google Play!
By Joe Hindy.
Friday, June 24, 2016
What happens if you don’t switch your smartphone to airplane mode during flight
What happens if you don’t switch your smartphone to airplane mode during flight
Here is what really happens if you don’t put your smartphone into flight mode/airplane mode when flying
You
may have traveled a lot by air and may have been told and warned to
switch your smartphone to flight mode or airplane mode. Have you ever
wondered why you are asked by the flight attendants on board to switch
your devices to airplane mode during transit? Did you ever imagine what
would happen if you didn’t put your smartphone on airplane mode when you
are up in the air?Most of us may feel it is unnecessary to switch to airplane mode during flight. Some of us even feel that doing so is a waste of time as it achieves nothing as it doesn’t interfere with plane’s electrical and telecommunication systems and is not a matter of life and death, some think it can cause occasional disturbance not leading to a crash for sure.
So, what is the truth? Let’s find out what exactly happens when passengers or crew don’t switch their phones to airplane mode during a flight!
Also, if you leave it on, it can annoy pilots and cause an unpleasant sound for air traffic controllers. A smartphone’s radio emissions can be very strong, up to 8W, which cause this noise due to parasitic demodulation. However, in a worst case scenario, repeated interference from mobiles could cause the crew to miss a crucial radio call from air traffic control.
“You may have heard that unpleasant noise from an audio system that occasionally happens when a mobile phone is nearby. I actually heard such noise on the radio while flying. It is not safety critical, but is annoying for sure.”
Those problems are something like the noise that can be heard when a smartphone rings near to a speaker: a slow, percussive thumping. But instead of coming out of a speaker it can be heard through the headsets that are worn by pilots.
Further, he also continues by saying that if 50 people on the plane did not turn their smartphone onto flight mode, it would cause a lot of “radio pollution.”
So, when you are flying next time, it is advisable to stick to the rules onboard.
By Kavita Iyer
Tuesday, June 21, 2016
China Beats US On Supercomputer List
View photos

In
2001, China had no presence on the list of the top 500 supercomputers
in the world. Today, the world's most populous country has the most
supercomputers on the list, including the world's fastest — and for the
first time ever it no longer relies on chips made by U.S. companies.
The
Sunway TaihuLight supercomputer based at the state-funded Chinese
Supercomputing Center in the city of Wuxi, Jiangsu province, a two-hour
drive from Shanghai. China already held the top spot on the list of
fastest supercomputers with the Tianhe-2, but that featured processors
built by Intel, a U.S. company.
However,
a chip built by the Shanghai High Performance IC Design Center
called SW26010 is capable of achieving 125.4 petaflops (Pflop/s).
That means it can carry out more than 125 quintillion calculations per
second. The SW26010 is comprised of more than 10 million processing
cores, and to put its performance in context, Tianhe-2 topped the list
in 2015 with a performance of 33.86 Pflops/s.
“As
the first number one system of China that is completely based on
homegrown processors, the Sunway TaihuLight system demonstrates the
significant progress that China has made in the domain of designing and
manufacturing large-scale computation systems,” Guangwen Yang, director
of the Chinese Supercomputing Center, told TOP500 News.
The
supercomputer will be used for research and engineering work in areas
such as climate, weather and earth systems modeling, life science
research, advanced manufacturing and data analytics.
The
list of the world's fastest 500 supercomputers is compiled by research
organization TOP500, and the list this year shows that for the first
time China has more supercomputers (167) on the list than the U.S.
(165), with Japan a distant third with just 29.
So how has China gone from supercomputer nobody to powerhouse in such a short time?
1. China's Government
China's
government wants to lessen (and where possible eradicate) the
dependence on overseas technology, specifically technology designed and
built in the U.S. To do this, it has invested heavily in research and
development such as the National Supercomputing Center to develop
homegrown solutions.
According
to Wall Street research firm Sanford C. Bernstein, the country buys
half of all the semiconductors produced in the world, but it doesn't
have a single domestic chipmaker among the world's biggest. For this
reason, China's government has told local media that it will pledge 1
trillion yuan ($152 billion) to help create a Chinese chip industry by
2025.
The Sunway TaihuLight is a major milestone on the road to creating this industry.

2. U.S. Embargo
In
addition to being spurred by its own government, the Chinese technology
industry was given a push by the U.S. government, too. In April
2015, the U.S. blocked high-end processors, such as Intel's Xeon Phi
chips, from being sold to a number of Chinese supercomputing centers.
The U.S. Department of Commerce never publicly said why the embargo was
in place, but the rules state certain items can be blocked if there
is "a significant risk of being or becoming involved in activities that
are contrary to the national security or foreign policy interests of the
United States."
The move precipitated a more concerted effort in China to develop and manufacture such chips domestically.
3. Money
While
the market for supercomputing chips is not huge, there is a huge market
for computer chips in general, and by showing that it can produce
processors capable of matching, and beating, those on offer from Intel
and IBM, China is now in a position to begin marketing its homegrown
solutions to server manufacturers and data centers — a market that is
currently dominated by Intel.
Companies
like Intel and Qualcomm know just how important the Chinese market
is and are aware of the risks a well-funded domestic chipmaker could
have on their bottom lines. To that end both companies have invested
heavily in China, partnering with local companies to bring manufacturing
to the country.
Monday, June 6, 2016
Universe expanding faster than expected
Universe expanding faster than expected
Astronomers have obtained the most precise measurement yet of how fast the universe is expanding, and it doesn’t agree with predictions based on other data and our current understanding of the physics of the cosmos.
A
Hubble Space Telescope image of the galaxy UGC 9391, one of the
galaxies in the new survey. UGC 9391 contains the two types of stars –
Cepheid variables and a Type 1a supernova – that astronomers used to
calculate a more precise Hubble constant. Click on the image to see the
red circles that mark the locations of Cepheids. The blue “X” denotes
the location of supernova 2003du, a Type Ia
Hubble Space Telescope. The observations
for this composite image were taken between 2012 and 2013 by Hubble’s
Wide Field Camera 3. (Image by NASA, ESA, and A. Riess [STScI/JHU])
“Maybe the universe is tricking us, or our understanding of the universe isn’t complete,” he added.
The cause could be the existence of another, unknown particle — perhaps an often-hypothesized fourth flavor of neutrino — or that the influence of dark energy (which accelerates the expansion of the universe) has increased over the 13.8 billion-year history of the universe. Or perhaps Einstein’s general theory of relativity, the basis for the Standard Model, is slightly wrong.
“This surprising finding may be an important clue to understanding those mysterious parts of the universe that make up 95 percent of everything and don’t emit light, such as dark energy, dark matter and dark radiation,” said the leader of the study, Nobel laureate Adam Riess, of the Space Telescope Science Institute and Johns Hopkins University, both in Baltimore. Riess is a former UC Berkeley post-doctoral fellow who worked with Filippenko.
The results, using data from the Hubble Space Telescope and the Keck I telescope in Hawaii, will appear in an upcoming issue of the Astrophysical Journal.
Afterglow of Big Bang
A few years ago, the European Space Agency’s Planck observatory — now out of commission — measured fluctuations in the cosmic background radiation to document the universe’s early history. Planck’s measurements, combined with the current Standard Model of physics, predicted an expansion rate today of 66.53 (plus or minus 0.62) kilometers per second per megaparsec. A megaparsec equals 3.26 million light-years.
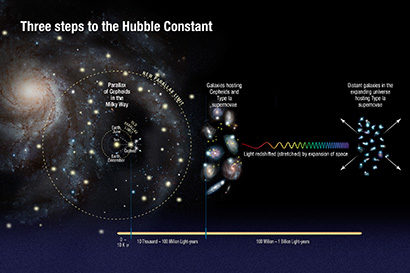
Astronomers
used the Hubble Space Telescope to measure the distances to a class of
pulsating stars called Cepheid variables to calibrate their true
brightness, so that they could be used as cosmic yardsticks to measure
distances to galaxies much farther away. This method is more precise
than the classic parallax technique. (Image courtesy of NASA, ESA, A.
Feild [STScI], and A. Riess [STScI/JHU])
The team looked for galaxies containing both a type of variable star called a Cepheid and Type Ia supernovae. Cepheid stars pulsate at rates that correspond to their true brightness (power), which can be compared with their apparent brightness as seen from Earth to accurately determine their distance and thus the distance of the galaxy. Type Ia supernovae, another commonly used cosmic yardstick, are exploding stars that flare with the same intrinsic brightness and are brilliant enough to be seen from much longer distances.
By measuring about 2,400 Cepheid stars in 19 nearby galaxies and comparing the apparent brightness of both types of stars, the researchers accurately determined the true brightness of the Type Ia supernovae. They then used this calibration to calculate distances to roughly 300 Type Ia supernovae in far-flung galaxies.
“We needed both the nearby Cepheid distances for galaxies hosting Type Ia supernovae and the distances to the 300 more-distant Type Ia supernovae to determine the Hubble constant,” Filippenko said. “The paper focuses on the 19 galaxies and getting their distances really, really well, with small uncertainties, and thoroughly understanding those uncertainties.”
Calibrating Cepheid variable stars
Using the Keck I 10-meter telescope in Hawaii, Filippenko’s group measured the chemical abundances of gases near the locations of Cepheid variable stars in the nearby galaxies hosting Type Ia supernovae. This allowed them to improve the accuracy of the derived distances of these galaxies, and thus to more accurately calibrate the peak luminosities of their Type Ia supernovae.
“We’ve done the world’s best job of decreasing the uncertainty in the measured rate of universal expansion and of accurately assessing the size of this uncertainty,” said Filippenko, “yet we find that our measured rate of expansion is probably incompatible with the rate expected from observations of the young universe, suggesting that there’s something important missing in our physical understanding of the universe.”
“If we know the initial amounts of stuff in the universe, such as dark energy and dark matter, and we have the physics correct, then you can go from a measurement at the time shortly after the Big Bang and use that understanding to predict how fast the universe should be expanding today,” said Riess. “However, if this discrepancy holds up, it appears we may not have the right understanding, and it changes how big the Hubble constant should be today.”
Aside from an increase in the strength with which dark energy is pushing the universe apart, and the existence of a new fundamental subatomic particle – a nearly speed-of-light particle called “dark radiation” – another possible explanation is that dark matter possesses some weird, unexpected characteristics. Dark matter is the backbone of the universe upon which galaxies built themselves into the large-scale structures seen today.
The Hubble observations were made with Hubble’s sharp-eyed Wide Field Camera 3 (WFC3), and were conducted by the Supernova H0 for the Equation of State (SHOES) team, which works to refine the accuracy of the Hubble constant to a precision that allows for a better understanding of the universe’s behavior.
The SHOES Team is still using Hubble to reduce the uncertainty in the Hubble constant even more, with a goal to reach an accuracy of 1 percent. Telescopes such as the European Space Agency’s Gaia satellite, and future telescopes such as the James Webb Space Telescope (JWST), an infrared observatory, and the Wide Field Infrared Space Telescope (WFIRST), also could help astronomers make better measurements of the expansion rate.
The Hubble Space Telescope is a project of international cooperation between NASA and the European Space Agency. NASA’s Goddard Space Flight Center in Greenbelt, Maryland, manages the telescope. The Space Telescope Science Institute (STScI) in Baltimore conducts Hubble science operations. STScI is operated for NASA by the Association of Universities for Research in Astronomy in Washington, D.C. The W. M. Keck Observatory in Hawaii is operated as a scientific partnership among the California Institute of Technology, the University of California and NASA.
Filippenko’s research was supported by NASA, the National
Science Foundation, the TABASGO Foundation, Gary and Cynthia Bengier and
the Christopher R. Redlich Fund.
Monday, May 23, 2016
Bayesian reasoning implicated in some mental disorders
From within the dark confines of the skull, the brain
builds its own version of reality. By weaving together expectations and
information gleaned from the senses, the brain creates a story about
the outside world. For most of us, the brain is a skilled storyteller,
but to spin a sensible yarn, it has to fill in some details itself.
“The brain is a guessing machine, trying at each moment of time to guess what is out there,” says computational neuroscientist Peggy Seriès.
Guesses just slightly off — like mistaking a smile for a smirk — rarely cause harm. But guessing gone seriously awry may play a part in mental illnesses such as schizophrenia, autism and even anxiety disorders, Seriès and other neuroscientists suspect. They say that a mathematical expression known as Bayes’ theorem — which quantifies how prior expectations can be combined with current evidence — may provide novel insights into pernicious mental problems that have so far defied explanation.
Bayes’ theorem “offers a new vocabulary, new tools
and a new way to look at things,” says Seriès, of the University of
Edinburgh.
Experiments guided by Bayesian math reveal that the guessing process differs in people with some disorders. People with schizophrenia, for instance, can have trouble tying together their expectations with what their senses detect. And people with autism and high anxiety don’t flexibly update their expectations about the world, some lab experiments suggest. That missed step can muddy their decision-making abilities.
Given the complexity of mental disorders such as schizophrenia and autism, it is no surprise that many theories of how the brain works have fallen short, says psychiatrist and neuroscientist Rick Adams of University College London. Current explanations for the disorders are often vague and untestable. Against that frustrating backdrop, Adams sees great promise in a strong mathematical theory, one that can be used to make predictions and actually test them.
“It’s really a step up from the old-style cognitive psychology approach, where you had flowcharts with boxes and labels on them with things like ‘attention’ or ‘reading,’ but nobody having any idea about what was going on in [any] box,” Adams says.
Applying math to mental disorders “is a very young field,” he adds, pointing to Computational Psychiatry, which plans to publish its first issue this summer. “You know a field is young when it gets its first journal.”
Bayes figured out a way to put numbers to this process. By combining probabilities that come from prior evidence and current observations, Bayes’ formula can be used to calculate an overall estimate of the likelihood that a given suspicion is true. A properly functioning brain seems to do this calculation intuitively, behaving in many cases like a skilled Bayesian statistician, some studies show (SN: 10/8/11, p. 18).
Story continues after graphic
This reckoning requires the brain to give the right
amount of weight to prior expectations and current information.
Depending on the circumstances, those weights change. When the senses
falter, for instance, the brain should lean more heavily on prior
expectations. Say the mail carrier comes each day at 4 p.m. On a stormy
afternoon when visual cues are bad, we rely less on sight and more on
prior knowledge to guess that the late-afternoon noise on the front
porch is probably the mail carrier delivering letters. In certain mental
illnesses, this flexible balancing act may falter.
People with schizophrenia often suffer from hallucinations and delusions, debilitating symptoms that arise when lines between reality and imagination blur. That confusion can lead to hearing voices that aren’t there and believing things that can’t possibly be true. These departures from reality could arise from differences in how people integrate new evidence with previous beliefs.
 There’s
evidence for such distorted calculations. People with schizophrenia
don’t fall for certain visual illusions that trick most people, for
instance. When shown a picture of the inside of a hollowed-out face
mask, most people’s brains mistakenly convert the image to a face that
pops outward off the page. People with schizophrenia, however, are more
likely to see the face as it actually is — a concave mask. In that
instance, people with schizophrenia give more weight to information
that’s coming from their eyes than to their expectation that noses
protrude from the rest of the face.
To complicate matters, the opposite can be true, too,
says neuropsychologist Chris Frith of the Wellcome Trust Centre for
Neuroimaging at University College London. “In this case, their prior is
too weak, but in other cases, their prior is too strong,” he says.
There’s
evidence for such distorted calculations. People with schizophrenia
don’t fall for certain visual illusions that trick most people, for
instance. When shown a picture of the inside of a hollowed-out face
mask, most people’s brains mistakenly convert the image to a face that
pops outward off the page. People with schizophrenia, however, are more
likely to see the face as it actually is — a concave mask. In that
instance, people with schizophrenia give more weight to information
that’s coming from their eyes than to their expectation that noses
protrude from the rest of the face.
To complicate matters, the opposite can be true, too,
says neuropsychologist Chris Frith of the Wellcome Trust Centre for
Neuroimaging at University College London. “In this case, their prior is
too weak, but in other cases, their prior is too strong,” he says.
In a recent study, healthy people and those who recently began experiencing psychosis, a symptom of schizophrenia, were shown confusing shadowy black-and-white images. Participants then saw color versions of the images that were easier to interpret. When shown the black-and-white images again, people with early psychosis were better at identifying the images, suggesting that they used their prior knowledge — the color pictures — to truly “see” the images. For people without psychosis, the color images weren’t as much help. That difference suggests that the way people with schizophrenia balance past knowledge and present observations is distinct from the behavior of people without the disorder. Sometimes the balance tips too far — in either direction.
In a talk at the annual Computational and Systems Neuroscience meeting in February in Salt Lake City, Seriès described the results of a different visual test: A small group of people with schizophrenia had to describe which way a series of dots were moving on a screen. The dots moved in some directions more frequently than others — a statistical feature that let the scientists see how well people could learn to predict the dots’ directions. The 11 people with schizophrenia seemed just as good at learning which way the dots were likely to move as the 10 people without, Seriès said. In this situation, people with schizophrenia seemed able to learn priors just fine.
But when another trick was added, a split between the two groups emerged. Sometimes, the dots were almost impossible to see, and sometimes, there were no dots at all. People with schizophrenia were less likely to claim that they saw dots when the screen was blank. Perhaps they didn’t hallucinate dots because of the medication they were on, Seriès says. In fact, very early results from unmedicated people with schizophrenia suggest that they actually see dots that aren’t there more than healthy volunteers.
 Preliminary
results so far on schizophrenia are sparse and occasionally
conflicting, Seriès admits. “It’s the beginning,” she says. “We don’t
understand much.”
Preliminary
results so far on schizophrenia are sparse and occasionally
conflicting, Seriès admits. “It’s the beginning,” she says. “We don’t
understand much.”
The research is so early that no straightforward story exists yet. But that’s not unexpected. “If 100 years of schizophrenia research have taught us anything, it’s that there’s not going to be a nice, simple explanation,” Adams says. But using math to describe how people perceive the world may lead to new hunches about how that process goes wrong in mental illnesses, he argues.
“You can instill expectations in subjects in many different ways, and you can control what evidence they see,” Adams says. Bayesian theory “tells you what they should conclude from those prior beliefs and that evidence.” If their conclusions diverge from predictions, scientists can take the next step. Brain scans, for instance, may reveal how the wrong answers arise. With a clear description of these differences, he says, “we might be able to measure people’s cognition in a new way, and diagnose their disorders in a new way.”
Another study supports the notion that sensory information takes priority in people with autism. People with and without autism were asked to judge whether a sight and a sound happened at the same time. They saw a white ring on a screen, and a tone played before, after or at the same time. Adults without autism were influenced by previous trials in which the ring and tone were slightly off. But adults with autism were not swayed by earlier trials, researchers reported in February in Scientific Reports.
This literal perception might get in the way of speech perception, Marco Turi of the University of Pisa in Italy and colleagues suggest. Comprehending speech requires a listener to mentally stitch together sights and sounds that may not arrive at the eyes and ears at the same time. Losing that flexibility could make speech harder to understand.
A different study found that children with autism perceive moving dots more clearly than children without autism (SN Online: 5/5/15). The brains of people with autism seem to prioritize incoming sensory information over expectations about how things ought to work. Elizabeth Pellicano of University College London and David Burr of the University of Western Australia in Perth described the concept in 2012 in an opinion paper in Trends in Cognitive Sciences. Intensely attuned to information streaming in from the senses, people with autism experience the world as “too real,” Pellicano and Perth wrote.
New data, however, caution against a too-simple explanation. In an experiment presented in New York City in April at the annual meeting of the Cognitive Neuroscience Society, 20 adults with and without autism had to quickly hit a certain key on a keyboard when they saw its associated target on a screen. Their job was made easier because the targets came in a certain sequence. All of the participants improved as they learned which keys to expect. But when the sequence changed to a new one, people with autism faltered. This result suggests that they learned prior expectations just fine, but had trouble updating them as conditions changed, said cognitive neuroscientist Owen Parsons of the University of Cambridge.
Story continues after graphic
 Distorted calculations — and the altered versions of
the world they create — may also play a role in depression and anxiety,
some researchers think. While suffering from depression, people may hold
on to distorted priors — believing that good things are out of reach,
for instance. And people with high anxiety can have trouble making good
choices in a volatile environment, neuroscientist Sonia Bishop of the
University of California, Berkeley and colleagues reported in 2015 in Nature Neuroscience.
Distorted calculations — and the altered versions of
the world they create — may also play a role in depression and anxiety,
some researchers think. While suffering from depression, people may hold
on to distorted priors — believing that good things are out of reach,
for instance. And people with high anxiety can have trouble making good
choices in a volatile environment, neuroscientist Sonia Bishop of the
University of California, Berkeley and colleagues reported in 2015 in Nature Neuroscience.
In their experiment, people had to choose a shape, which sometimes came with a shock. People with low anxiety quickly learned to avoid the shock, even when the relationship between shape and shock changed. But people with high anxiety performed worse when those relationships changed, the researchers found. “High-anxious individuals didn’t seem able to adjust their learning to handle how volatile or how stable the environment was,” Bishop says.
Scientists can’t yet say what causes this difficulty
adjusting to a new environment in anxious people and in people with
autism. It could be that once some rule is learned (a sequence of
computer keys, or the link between a shape and a shock), these two
groups struggle to update that prior with newer information.
This rigidity might actually contribute to anxiety in the first place, Bishop speculates. “When something unexpected happens that is bad, you wouldn’t know how to respond,” and that floundering “is likely to be a huge source of anxiety and stress.”
Computational psychiatrist Quentin Huys of the University of Zurich is one of those people. Math can help clarify mental illnesses in a way that existing approaches can’t, he says. In the March issue of Nature Neuroscience, Huys and colleagues argued that math can demystify psychiatric disorders, and that thinking of the brain as a Bayesian number cruncher might lead to a more rigorous understanding of mental illness. Huys says that a computational approach is essential. “We can’t get away without it.” If people with high anxiety perform differently on a perceptual test, then that test could be used to both diagnose people and monitor how well a treatment works, for instance.
Scientists hope that a deeper description of mental illnesses may lead to clearer ways to identify a disorder, chart how well treatments work and even improve therapies. Bishop raises the possibility of developing apps to help people with high anxiety evaluate situations — outsourcing the decision making for people who have trouble. Frith points out that cognitive behavioral therapy could help depressed people recalculate their experiences by putting less weight on negative experiences and perhaps breaking out of cycles of despondence.
Beyond these potential interventions, simply explaining to people how their brains are working might ease distress, Adams says. “If you can give people an explanation that makes sense of some of the experiences they’ve had, that can be a profoundly helpful thing,” he says. “It destigmatizes the experience.”
This article appears in the May 28, 2016, Science News with the headline, "Misguided math: Faulty Bayesian reasoning may explain some mental disorders."
“The brain is a guessing machine, trying at each moment of time to guess what is out there,” says computational neuroscientist Peggy Seriès.
Guesses just slightly off — like mistaking a smile for a smirk — rarely cause harm. But guessing gone seriously awry may play a part in mental illnesses such as schizophrenia, autism and even anxiety disorders, Seriès and other neuroscientists suspect. They say that a mathematical expression known as Bayes’ theorem — which quantifies how prior expectations can be combined with current evidence — may provide novel insights into pernicious mental problems that have so far defied explanation.
Expectations
People have assumptions about the world, which are either inborn or learned early in life. For example:
- Light comes from above.
- Noses stick out.
- Objects move slowly.
- Background images are uniformly colored.
- Other people’s gazes are directed at us.
Experiments guided by Bayesian math reveal that the guessing process differs in people with some disorders. People with schizophrenia, for instance, can have trouble tying together their expectations with what their senses detect. And people with autism and high anxiety don’t flexibly update their expectations about the world, some lab experiments suggest. That missed step can muddy their decision-making abilities.
Given the complexity of mental disorders such as schizophrenia and autism, it is no surprise that many theories of how the brain works have fallen short, says psychiatrist and neuroscientist Rick Adams of University College London. Current explanations for the disorders are often vague and untestable. Against that frustrating backdrop, Adams sees great promise in a strong mathematical theory, one that can be used to make predictions and actually test them.
“It’s really a step up from the old-style cognitive psychology approach, where you had flowcharts with boxes and labels on them with things like ‘attention’ or ‘reading,’ but nobody having any idea about what was going on in [any] box,” Adams says.
Applying math to mental disorders “is a very young field,” he adds, pointing to Computational Psychiatry, which plans to publish its first issue this summer. “You know a field is young when it gets its first journal.”
A mind for math
Bayesian reasoning may be new to the mental illness scene, but the math itself has been around for centuries. First described by the Rev. Thomas Bayes in the 18th century, this computational approach truly embraces history: Evidence based on previous experience, known as a “prior,” is essential to arriving at a good answer, Bayes argued. He may have been surprised to see his math meticulously applied to people with mental illness, but the logic holds. To make a solid guess about what’s happening in the world, the brain must not rely just on current input from occasionally unreliable senses. The brain must also use its knowledge about what has happened before. Merging these two streams of information correctly is at the heart of perceiving the world as accurately as possible.Bayes figured out a way to put numbers to this process. By combining probabilities that come from prior evidence and current observations, Bayes’ formula can be used to calculate an overall estimate of the likelihood that a given suspicion is true. A properly functioning brain seems to do this calculation intuitively, behaving in many cases like a skilled Bayesian statistician, some studies show (SN: 10/8/11, p. 18).
Story continues after graphic
Where there's smoke
The example below shows how Bayesian reasoning is applied to a question of the probability of a dangerous fire.


People with schizophrenia often suffer from hallucinations and delusions, debilitating symptoms that arise when lines between reality and imagination blur. That confusion can lead to hearing voices that aren’t there and believing things that can’t possibly be true. These departures from reality could arise from differences in how people integrate new evidence with previous beliefs.

In a recent study, healthy people and those who recently began experiencing psychosis, a symptom of schizophrenia, were shown confusing shadowy black-and-white images. Participants then saw color versions of the images that were easier to interpret. When shown the black-and-white images again, people with early psychosis were better at identifying the images, suggesting that they used their prior knowledge — the color pictures — to truly “see” the images. For people without psychosis, the color images weren’t as much help. That difference suggests that the way people with schizophrenia balance past knowledge and present observations is distinct from the behavior of people without the disorder. Sometimes the balance tips too far — in either direction.
In a talk at the annual Computational and Systems Neuroscience meeting in February in Salt Lake City, Seriès described the results of a different visual test: A small group of people with schizophrenia had to describe which way a series of dots were moving on a screen. The dots moved in some directions more frequently than others — a statistical feature that let the scientists see how well people could learn to predict the dots’ directions. The 11 people with schizophrenia seemed just as good at learning which way the dots were likely to move as the 10 people without, Seriès said. In this situation, people with schizophrenia seemed able to learn priors just fine.
But when another trick was added, a split between the two groups emerged. Sometimes, the dots were almost impossible to see, and sometimes, there were no dots at all. People with schizophrenia were less likely to claim that they saw dots when the screen was blank. Perhaps they didn’t hallucinate dots because of the medication they were on, Seriès says. In fact, very early results from unmedicated people with schizophrenia suggest that they actually see dots that aren’t there more than healthy volunteers.

The research is so early that no straightforward story exists yet. But that’s not unexpected. “If 100 years of schizophrenia research have taught us anything, it’s that there’s not going to be a nice, simple explanation,” Adams says. But using math to describe how people perceive the world may lead to new hunches about how that process goes wrong in mental illnesses, he argues.
“You can instill expectations in subjects in many different ways, and you can control what evidence they see,” Adams says. Bayesian theory “tells you what they should conclude from those prior beliefs and that evidence.” If their conclusions diverge from predictions, scientists can take the next step. Brain scans, for instance, may reveal how the wrong answers arise. With a clear description of these differences, he says, “we might be able to measure people’s cognition in a new way, and diagnose their disorders in a new way.”
Now vs. then
The way the brain combines incoming sensory information with existing knowledge may also be different in autism, some researchers argue. In some cases, people with autism might put excess weight on what their senses take in about the world and rely less on their expectations. Old observations fit with this idea. In the 1960s, psychologists had discovered that children with autism were just as good at remembering nonsense sentences (“By is go tree stroke lets”) as meaningful ones (“The fish swims in the pond”). Children without autism struggled to remember the non sequiturs. But the children with autism weren’t thrown by the random string of words, suggesting that their expectations of sentence meaning weren’t as strong as their ability to home in on each word in the series.Another study supports the notion that sensory information takes priority in people with autism. People with and without autism were asked to judge whether a sight and a sound happened at the same time. They saw a white ring on a screen, and a tone played before, after or at the same time. Adults without autism were influenced by previous trials in which the ring and tone were slightly off. But adults with autism were not swayed by earlier trials, researchers reported in February in Scientific Reports.
This literal perception might get in the way of speech perception, Marco Turi of the University of Pisa in Italy and colleagues suggest. Comprehending speech requires a listener to mentally stitch together sights and sounds that may not arrive at the eyes and ears at the same time. Losing that flexibility could make speech harder to understand.
A different study found that children with autism perceive moving dots more clearly than children without autism (SN Online: 5/5/15). The brains of people with autism seem to prioritize incoming sensory information over expectations about how things ought to work. Elizabeth Pellicano of University College London and David Burr of the University of Western Australia in Perth described the concept in 2012 in an opinion paper in Trends in Cognitive Sciences. Intensely attuned to information streaming in from the senses, people with autism experience the world as “too real,” Pellicano and Perth wrote.
New data, however, caution against a too-simple explanation. In an experiment presented in New York City in April at the annual meeting of the Cognitive Neuroscience Society, 20 adults with and without autism had to quickly hit a certain key on a keyboard when they saw its associated target on a screen. Their job was made easier because the targets came in a certain sequence. All of the participants improved as they learned which keys to expect. But when the sequence changed to a new one, people with autism faltered. This result suggests that they learned prior expectations just fine, but had trouble updating them as conditions changed, said cognitive neuroscientist Owen Parsons of the University of Cambridge.
Story continues after graphic
Memory test
In a 1967 study, children with autism were just as good at remembering nonsense strings of words as they were at remembering sentences. The results suggest that they had weaker expectations about meaningful sentences.
In their experiment, people had to choose a shape, which sometimes came with a shock. People with low anxiety quickly learned to avoid the shock, even when the relationship between shape and shock changed. But people with high anxiety performed worse when those relationships changed, the researchers found. “High-anxious individuals didn’t seem able to adjust their learning to handle how volatile or how stable the environment was,” Bishop says.
Stress shutdown
People with higher levels of anxiety (light blue)
learned less from shocks (measured by changes in pupil size) when the
environment changed than people with low anxiety (dark blue).
 Source: Michael Browning et al/Nature Neuroscience 2015.
Source: Michael Browning et al/Nature Neuroscience 2015.

This rigidity might actually contribute to anxiety in the first place, Bishop speculates. “When something unexpected happens that is bad, you wouldn’t know how to respond,” and that floundering “is likely to be a huge source of anxiety and stress.”
Recalculating
“There’s been a lot of frustration with a failure to make progress” on psychiatric disorders, Bishop says. Fitting mathematical theories to the brain may be a way to move forward. Researchers “are very excited about computational psychiatry in general,” she says.Computational psychiatrist Quentin Huys of the University of Zurich is one of those people. Math can help clarify mental illnesses in a way that existing approaches can’t, he says. In the March issue of Nature Neuroscience, Huys and colleagues argued that math can demystify psychiatric disorders, and that thinking of the brain as a Bayesian number cruncher might lead to a more rigorous understanding of mental illness. Huys says that a computational approach is essential. “We can’t get away without it.” If people with high anxiety perform differently on a perceptual test, then that test could be used to both diagnose people and monitor how well a treatment works, for instance.
Scientists hope that a deeper description of mental illnesses may lead to clearer ways to identify a disorder, chart how well treatments work and even improve therapies. Bishop raises the possibility of developing apps to help people with high anxiety evaluate situations — outsourcing the decision making for people who have trouble. Frith points out that cognitive behavioral therapy could help depressed people recalculate their experiences by putting less weight on negative experiences and perhaps breaking out of cycles of despondence.
Beyond these potential interventions, simply explaining to people how their brains are working might ease distress, Adams says. “If you can give people an explanation that makes sense of some of the experiences they’ve had, that can be a profoundly helpful thing,” he says. “It destigmatizes the experience.”
This article appears in the May 28, 2016, Science News with the headline, "Misguided math: Faulty Bayesian reasoning may explain some mental disorders."
Friday, May 20, 2016
Military Apologizes After Drone Strike Intended For Yemeni ISIS Base Accidentally Hits West Palm Beach Wedding
WASHINGTON—Attributing the incident to an unfortunate and
highly out-of-the-ordinary technological malfunction, officials at the
Pentagon apologized this week after a drone strike intended for an ISIS
stronghold in the Middle East nation of Yemen accidentally hit a wedding
in West Palm Beach, FL, killing 17. “Credible information from
operatives on the ground indicated a high-value target on the southern
outskirts of Sana’a, however our Hellfire missiles veered some 7,700
miles off target and, regrettably, struck the Epstein-Miller wedding at
the Breakers Resort and Spa,” said U.S. Air Force Chief of Staff Gen.
Mark Welsh, who added that while the military always attempts to
minimize collateral damage inflicted by drones, occasional domestic
tragedies such as this one do occur from time to time, before noting
that the Pentagon was offering “generous” condolence payments to
grieving loved ones for each guest and member of the Tom Vilone
Celebration Band killed. “To the families of Blake and Natalie, you have
our deepest sympathies for the loss of Aunt Jessica, Grandpa Pete, and
the other relatives and friends who died in this terrible accident. And
we want to assure everyone that the U.S. is committed to fully
rebuilding the affected pool and ballroom facilities in a prompt
fashion.” Critics of U.S. military policy said the latest incident of
civilian deaths due to a UAV strike would only serve to further
radicalize residents of the restive Miami-Dade–Broward–Palm Beach region
against the United States government.
A who's who at Brooklyn's coolest innovation hub
Aerobo
Aerobo is the first FAA-approved drone operator in New York and the only company in the country operating drones on such a large scale. More specifically, though: The company makes flying robots.

"Having thick concrete walls is important," says company CMO Jon Ollwerther, above the clamor of machinery on the other side of the wall. "Having an office in Midtown Manhattan was not an option."
Aerobo CEO and co-founder Brian Streem counts Industry City's collegial, collaborative vibe as a big part of why he loves having their office here. In fact, when Aerobo first moved into the space, they borrowed WiFi from the people across the hall while getting their own connection set up. It's the modern equivalent of borrowing a cup of sugar.
Material Wrld
As co-founders of the luxury fashion trade-in company Material Wrld, Jie Zheng and Rie Yano have a mutual love for how the digital age can support their love for fashion. The friends, who met at Harvard Business School, both have a background in fashion e-commerce and were inspired to start their company when they realized the tired consignment store model of re-sale deserved an upgrade.
By locating operations at Industry City, Material Wrld has been able to keep inventory and operations all under one roof. It's a smart and economical move for a startup looking to streamline the process, learn from challenges that arise on site and become more efficient.

"There's a really great atmosphere here where you can create, meet and collaborate with other companies," Yano says.
Danielle Trofe Design
Though Danielle Trofe's studio may be small — all told, it's just about 250 square feet — her ideas are big. Trofe creates sustainable solutions for everyday needs, using eco-friendly materials and techniques in a range of creative ways. Her most recent endeavor is MushLume, a line of lamps grown from mushroom mycelium.Trofe's goal is to challenge how objects are made, how the materials are used and where they wind up at the end of their lives. Each of the organic lampshades in her collection is made from a rapidly renewable resource — a combination of corn stalk, seed husk and hemp held together with liquid mushroom mycelium that grows and solidifies — and is completely biodegradable. (Watch a video about her process here.)
At the heart of everything she does, from the mushroom lamps to a family of hydroponic vertical planters, is a curiosity for exploring how science, technology and design can come together in new and exciting ways.

"I like this idea of, 'Let's see how things are actually made.' Having that open-door, open-window policy is kind of nice," Trofe says.
Coinspace
Walk into the Coinspace headquarters and it’s easy to see that founder, Solomon Lederer, is a fan of how traditional models can be re-invented in new ways. Along one wall is a gallery of framed currency, from a One Hundred Trillion Zimbabwean Dollar, Euros and a Saudi Arabian Riyal note to $100,000 worth of Monopoly money. Also on the wall is a Bitcoin paper wallet, which is central to the operation.

Lederer says he loves Industry City because of its convenience and amenities, like the popular food halls, and the low rents in comparison to Manhattan. After all, money talks.

Image: Industry City
HERO
It's an exciting time for HERO, manufacturers of a smart pill management device that’s about to go into production. At the company's 8,000 square foot space in Industry City, boxes of parts and shipping materials sit by a row of tables that will soon become the assembly line. Further back is a machine shop of sorts, where engineers design, test and build the electronic brains of the operation. Deeper still is the actual operations office, where a row of photos hang on the wall illustrating their customer segments.HERO uses a patented pick and drop mechanism to deliver daily pills and vitamins, with a user-friendly interface and corresponding app that allows customers to set reminders and check in on loved ones to ensure medication is taken properly. The device also includes optional password protection to keep pills safe and secure.
Founder Kal Vepuri says that moving into the enormous space at Industry City a year ago has allowed the company to rapidly grow as they ramp up production, attracting talent nearby from Brooklyn and the rest of New York.
"[Industry City] allows us to have sufficient space for engineering, testing and doing research and development around a physical device, plus storing materials and assembling those devices," Vepuri says.
He also loves being in such an inspired community, working just down the hall from other entrepreneurs, makers and progressive thinkers.
"It was important to us to have a community doing innovative and progressive projects," he says.
Friday, March 18, 2016
Hackers strike Bank of Uganda accounts, try to steal 24,157,808.50 US Dollar
Ugandan government officials and hackers have since last July attempted
four times to siphon USh81 billion (Sh2.45 billion) through the Uganda
central bank. However some monies of the money that had successfully been wired to Hong Kong
and UAE was retrieved through inter-bank procedures, the latest being $8 million (Sh800
million) transferred on February 26, 2016. The accounts targeted were those of the
largest budget holders, among them the Defence, Energy and Agriculture ministries as
well as the Uganda National Roads Authority (UNRA). “The matter is the subject of an active investigation, so until that process ends we are not in a position to offer the details you are requesting for,” said Bank of Uganda communications director Christine Alupo. “Yes, indeed all the funds were recovered from the United Arab Emirates and Hong Kong and are back in the custody of the Bank of Uganda.”
The first attempt aimed at the biggest amount happened in July 2015 and $12 million (Sh1.2 billion) was targeted. The plot was foiled, and the masterminds went below the radar, re-emerging in December 2015 to try to steal $2 million (Sh200 million). A month later, in January 2016, they made
another attempt to fork out Sh800 million but were detected in time before returning
to compromise the system last month. Although the Ministry of Finance first notified
Uganda Police of the breaches 10 months ago, its detectives did not act immediately,
prompting the military, whose budget was targeted, to swing into action and arrest three
suspects who are in police custody. Police spokesperson Fred Enanga declined
to comment when asked why the UPDF had taken over the sensitive inquiries amid allegations
that police was compromised. Technocrats stole Ministry of Finance spokesman Jim Mugunga
said: “This is an ongoing investigation and our expectation is that the security agencies
involved are doing their work.” He was non-committal on the reported
past attempts, saying he believes investigators will unearth all breaches.
Government officials are believed to have shared passwords with foreign-based techsavvy
individuals, profiled the accounts with huge credits to stage the theft. All the Integrated Financial Management System transactions originated from the Ministry of Finance and processed through Bank of Uganda and the money was to be wired to fictitious companies in either Hong Kong or the United Arab Emirates. It is unclear how non-existent entities indicated in the documents held accounts, raising suspicion of possible collusion between host banks and the masterminds.
The fraud comes three years after the government instituted new financial integrity
measures to seal loopholes, following the 2012 scandal in which technocrats in the
Office of the Prime Minister stole in excess of USh60 billion (Sh1.8 billion) that development partners had pooled to rebuild war-scarred northern Uganda. HEIST Three suspected hackers arrested, $8m wired to Hong Kong and UAE retrieved.
four times to siphon USh81 billion (Sh2.45 billion) through the Uganda
central bank. However some monies of the money that had successfully been wired to Hong Kong
and UAE was retrieved through inter-bank procedures, the latest being $8 million (Sh800
million) transferred on February 26, 2016. The accounts targeted were those of the
largest budget holders, among them the Defence, Energy and Agriculture ministries as
well as the Uganda National Roads Authority (UNRA). “The matter is the subject of an active investigation, so until that process ends we are not in a position to offer the details you are requesting for,” said Bank of Uganda communications director Christine Alupo. “Yes, indeed all the funds were recovered from the United Arab Emirates and Hong Kong and are back in the custody of the Bank of Uganda.”
The first attempt aimed at the biggest amount happened in July 2015 and $12 million (Sh1.2 billion) was targeted. The plot was foiled, and the masterminds went below the radar, re-emerging in December 2015 to try to steal $2 million (Sh200 million). A month later, in January 2016, they made
another attempt to fork out Sh800 million but were detected in time before returning
to compromise the system last month. Although the Ministry of Finance first notified
Uganda Police of the breaches 10 months ago, its detectives did not act immediately,
prompting the military, whose budget was targeted, to swing into action and arrest three
suspects who are in police custody. Police spokesperson Fred Enanga declined
to comment when asked why the UPDF had taken over the sensitive inquiries amid allegations
that police was compromised. Technocrats stole Ministry of Finance spokesman Jim Mugunga
said: “This is an ongoing investigation and our expectation is that the security agencies
involved are doing their work.” He was non-committal on the reported
past attempts, saying he believes investigators will unearth all breaches.
Government officials are believed to have shared passwords with foreign-based techsavvy
individuals, profiled the accounts with huge credits to stage the theft. All the Integrated Financial Management System transactions originated from the Ministry of Finance and processed through Bank of Uganda and the money was to be wired to fictitious companies in either Hong Kong or the United Arab Emirates. It is unclear how non-existent entities indicated in the documents held accounts, raising suspicion of possible collusion between host banks and the masterminds.
The fraud comes three years after the government instituted new financial integrity
measures to seal loopholes, following the 2012 scandal in which technocrats in the
Office of the Prime Minister stole in excess of USh60 billion (Sh1.8 billion) that development partners had pooled to rebuild war-scarred northern Uganda. HEIST Three suspected hackers arrested, $8m wired to Hong Kong and UAE retrieved.
Tuesday, February 16, 2016
4 things you should be doing right now so you won't get hacked
4 things you should be doing right now so you won't get hacked
Cybercrime is a multi billion-dollar racket that affects corporations and individuals alike, but there are a few simple steps everyone can implement to protect against it.“If you’re a target, which honestly most companies are, then you really have to depend on taking some basic measures," says Kyle Lady, a research and development engineer with Duo Security.
Tech Insider spoke with Lady recently about how hackers infiltrate systems and what the best methods are for stopping them. Here's what he recommends.
Use passwords with at least 14 characters that can't be found in the dictionary.
The 25 worst passwords of 2015 include entries like "123456," "football," and "password," and these can all be easily guessed by an attacker. And we're not talking about a hacker typing in different passwords until they get it right; most have software that can guess hundreds and thousands of passwords a minute.So it's best to use something much stronger. "If I can find your password in a dictionary, so can an attacker," Lady says.
Lady recommends using a password with at least 14 characters (he uses at least 24) which has a number of uppercase and lowercase letters, and symbols in it. A password like "SYd#2n3l_!p4ss" — that has no real meaning and plenty of symbols to throw off a hacker — is going to be a lot better to use. But even using a phrase, like "this password security thing works," is going to be stronger than most.
"It’s going to be real hard [for an attacker]," Lady said. "Someone is going to expend a lot of resources just to guess that password by trying over and over."
But there's also a problem for the user: Memorizing that password full of hard-to-remember characters.
Use a password manager so you won't have to remember all of them.
A password manager like LastPass or 1Password can securely store all of your passwords for everything from your email to bank account in one spot, so you don't need to remember each one. Which is great, since Lady recommends using different passwords for your various accounts.Instead of coming up with a strong password filled with various symbols and letters yourself, most password managers can generate very strong passwords for you, encrypt them, and keep it on file, "so you don’t have to have them written down," Lady says.
Then, you only need to come up with one really strong master password.
Turn on two-factor authentication and your account will remain secure even if your password is hacked.
“Even weak passwords aren’t the end of the world, if you’re using two-factor authentication," Lady says.Two-factor authentication is becoming standard for password security. With two-factor, a user enters their password, then goes through a second round of screening, usually by entering in a code they received in a text message. For the most part, this second step would stop most hackers in their tracks, since they'd have to steal your phone in order to proceed.
“It’s becoming a standard option, but most people don’t enable it," Lady says, noting that most people are too lazy to do so. You can usually find two-step authorization in your account settings. It's available on Facebook, Twitter, Gmail, Snapchat, and a ton of other services — just make sure you actually turn it on.
Google A screenshot of Google's two-step authentication
Be especially wary of emails asking you to do something, or phone calls about the security of your accounts.
About 91% of targeted cyber attacks begin with a "spear-phishing" email, a trick designed to get a specific person to click on a link, give up their password, or download malware. These types of emails are designed to look like the real thing, and are really hard to judge at first glance.A scammer might email saying your PayPal account has been hacked, and you need to update your password. But once you click the link, you are actually giving them your password, not changing it. Lady says the key is to make sure you are on a legitimate page like paypal.com, and not a scam site with an address like www.paypalsecurity.xyz.
"If there’s any doubt in your mind, essentially, trust but verify," Lady said.
The same goes for suspicious phone calls. Hackers often use "social engineering" to convince a person to help them. So it's important to remain skeptical of calls from people claiming to be customer service representatives, since most companies don't call out, and almost all will never ask for passwords.
“I could be tech support with a cell phone in ten minutes and go around asking for passwords," Lady said.
Subscribe to:
Posts (Atom)
